Russia’s invasion of Ukraine has put the world on alert. Once again, the White House is warning Americans to protect themselves – and their business – from potential cyber threats that may come in retaliation to U.S.-led actions.
Secretary of Homeland Security Alejandro N. Mayorkas released the following statement on cybersecurity preparedness:
“As the Russian Government explores options for potential cyberattacks against the United States, the Department of Homeland Security continues to work closely with our partners across every level of government, in the private sector, and with local communities to protect our country’s networks and critical infrastructure from malicious cyber activity,” Mayorkas said. “Organizations of every size and across every sector should continue enhancing their cybersecurity defenses.”
Mayorkas said organizations can visit CISA.gov/Shields-Up for best practices on how to protect their networks, and they should report anomalous cyber activity and/or cyber incidents to [email protected] or (888) 282-0870, or to an FBI field office.
“DHS will continue to share timely and actionable information and intelligence to ensure our partners and the public have the tools they need to keep our communities safe and secure and increase nationwide cybersecurity preparedness.”
The White House began prioritizing strengthening cyber defense the day the administration took office. That work accelerated last November as Russia became more aggressive towards Ukraine.
While the government is providing resources and tools to help with cybersecurity defense, the burden falls on the private sector to ensure their own safety.
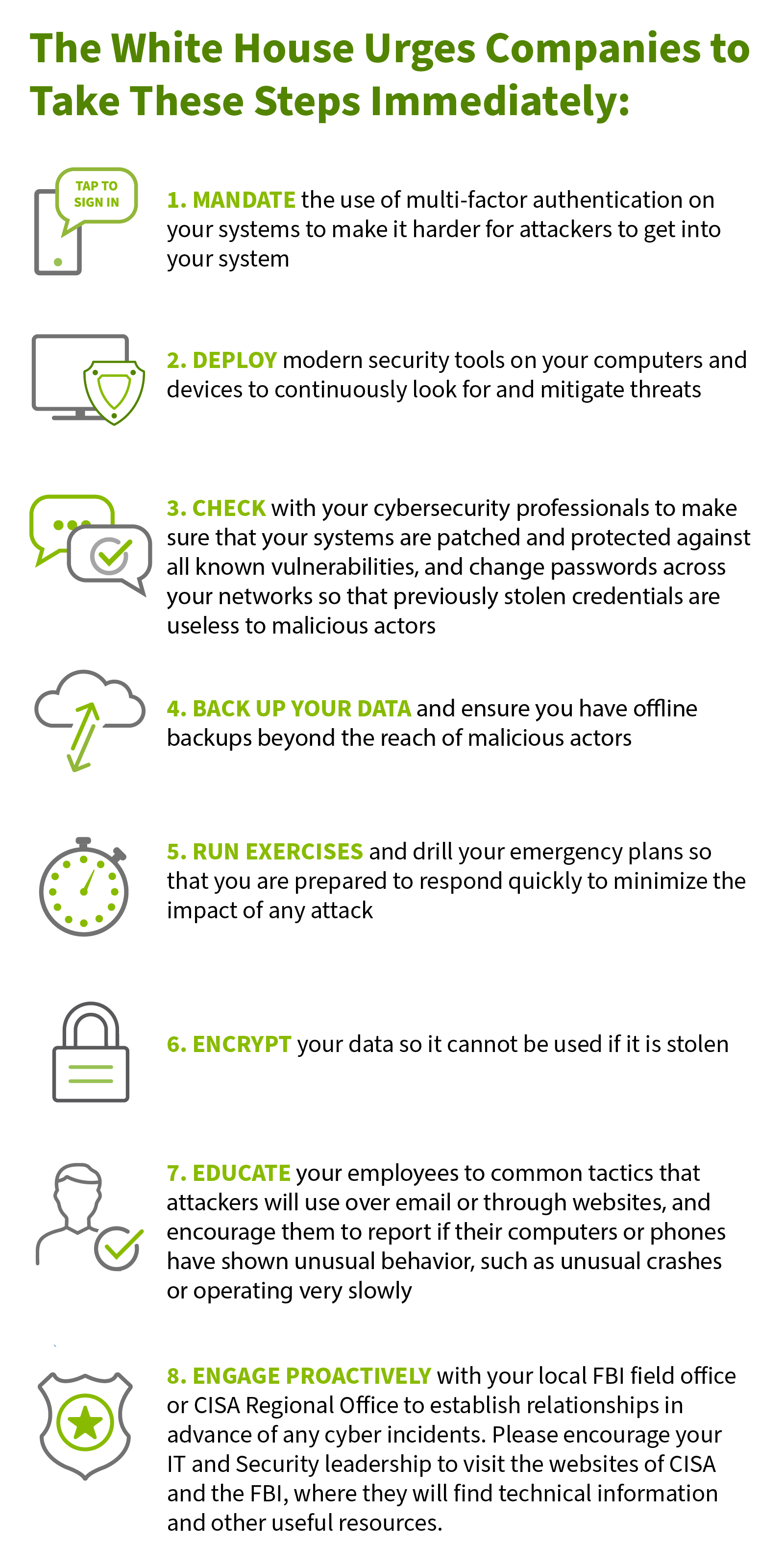 click to download PDF
click to download PDF
The White House added that Americans must focus on bolstering cybersecurity over the long term by encouraging technology and software companies to:
- Build security into products from the ground up — “bake it in, don’t bolt it on” — to protect both intellectual property and customer privacy.
- Develop software only on a system that is highly secure and accessible only to those actually working on a particular project. This will make it much harder for an intruder to jump from system to system and compromise a product or steal your intellectual property.
- Use modern tools to check for known and potential vulnerabilities. Developers can fix most software vulnerabilities — if they know about them. There are automated tools that can review code and find most coding errors before software ships, and before a malicious actor takes advantage of them.
- Software developers are responsible for all code used in their products, including open-source code. Most software is built using many different components and libraries, much of which is open source. Make sure developers know the provenance (i.e., origin) of components they are using and have a “software bill of materials” in case one of those components is later found to have a vulnerability so you can rapidly correct it.
- Implement the security practices mandated in the President’s Executive Order, Improving our Nation’s Cybersecurity. Pursuant to that EO, all software the U.S. government purchases is now required to meet security standards in how it is built and deployed.
The information presented is general in nature and should not be considered, legal, accounting or tax advice. Regions reminds its customers that they should be vigilant about fraud and security and that they are responsible for taking action to protect their computer systems. Fraud prevention requires a continuous review of your policies and practices, as the threat evolves daily. There is no guarantee that all fraudulent transactions will be prevented or that related financial losses will not occur. Visit regions.com/STOPFRAUD or speak with your Banker for further information on how you can help prevent fraud.